The MCP Gateway for Secure and Governed Tool Access
Engineered for your enterprise: secure, compliant, fully governed. Deploy anywhere with confidence, in your VPC, on site or isolated networks.
See the MCP Gateway in Action
This short walkthrough shows how MCPX centralizes tool usage for AI agents: simplifying access, applying policy guardrails, and providing live visibility into every agentic workflow.
The Gateway Architecture
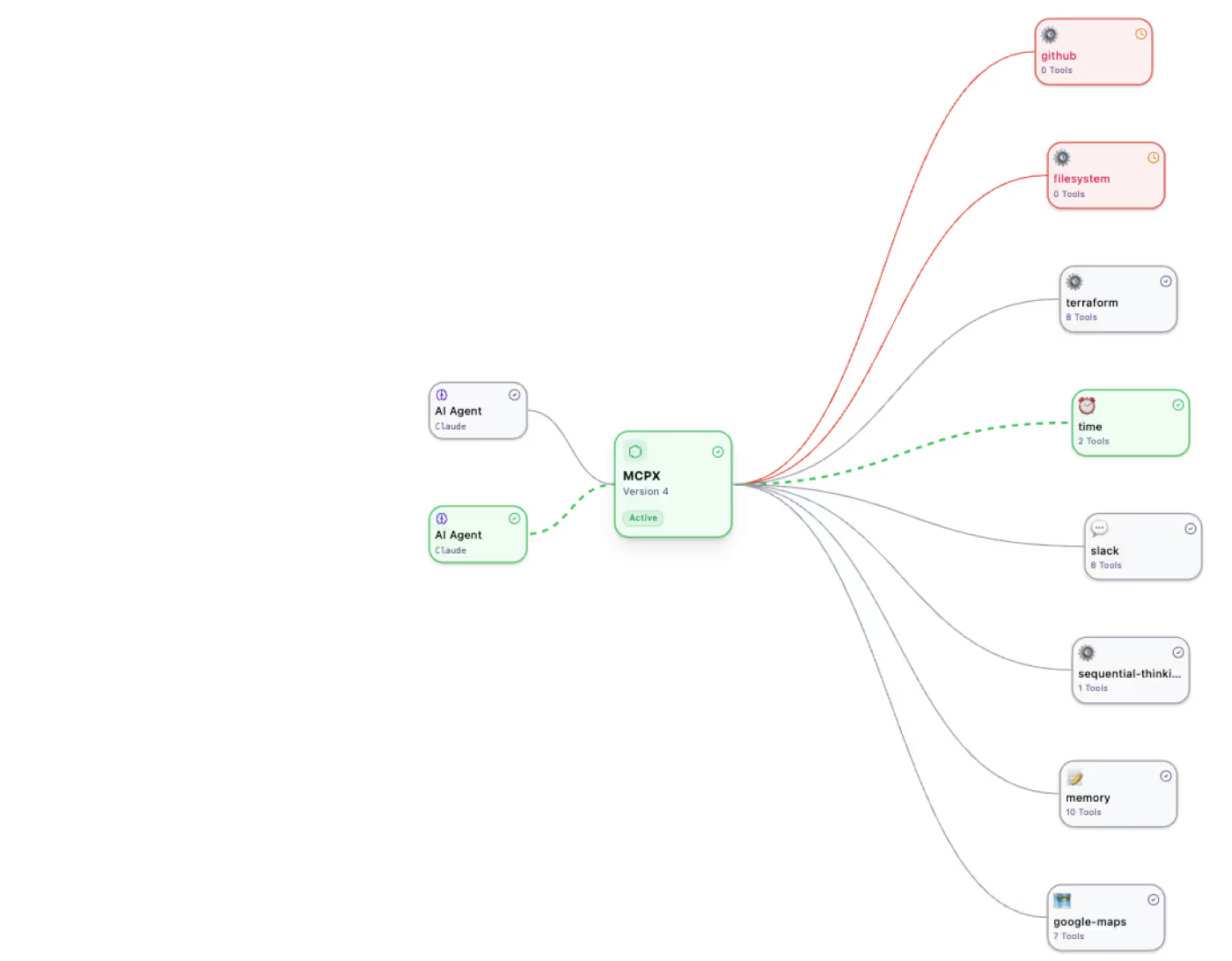
The MCP Gateway sits between AI agents and MCP servers, acting as a unified gateway for all tool invocations. It intercepts, authenticates, and governs traffic using policies defined by the organization.


.avif)
Unlock Safe and Scalable MCP Adoption
Unify Access to All MCP Servers
Expose a single gateway to access both local and remote MCP servers, with built-in service discovery.
Avoid per-agent integration or siloed deployments - connect once and govern everywhere.
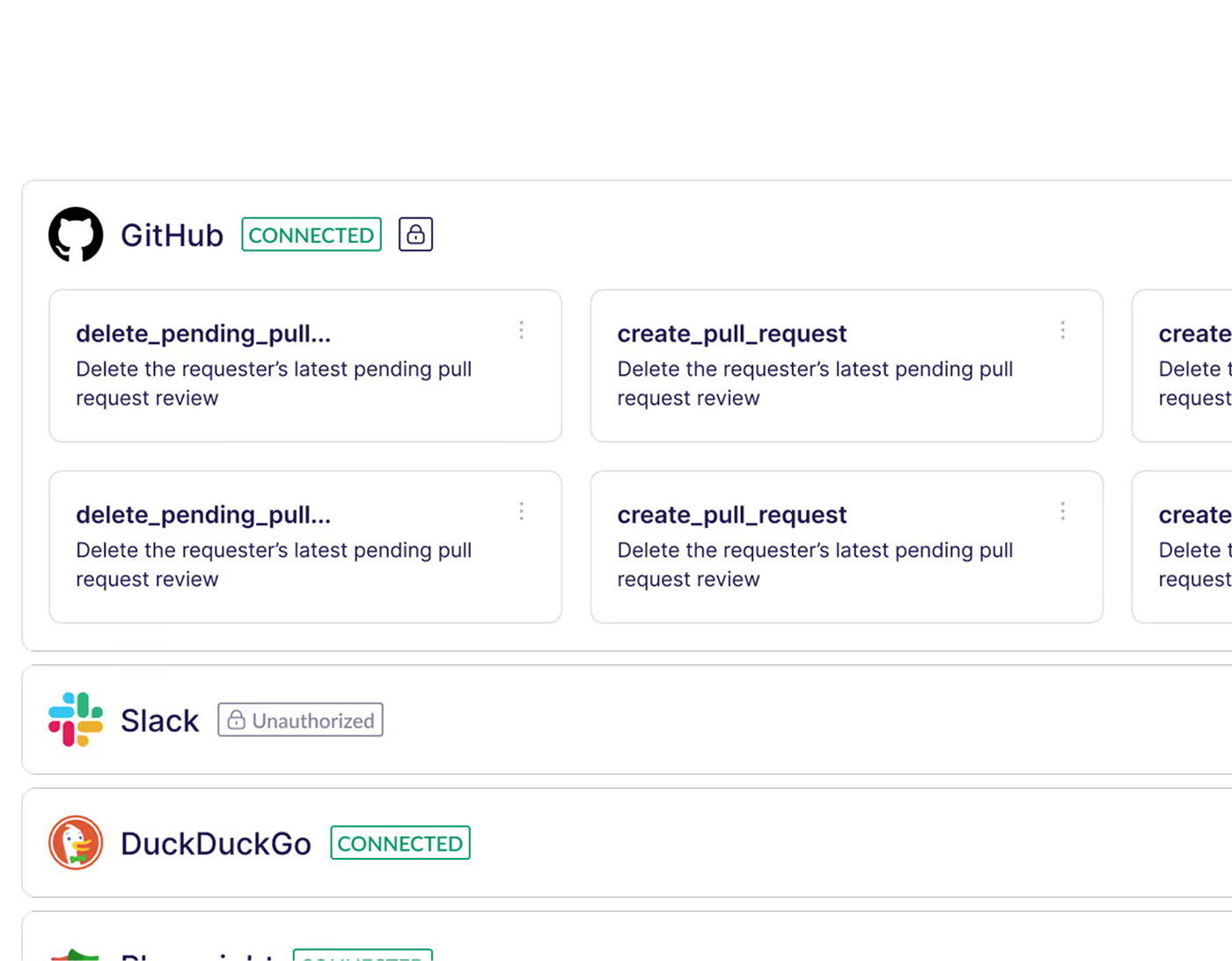
Enforce Authentication and Fine-Grained Access Controls
Control who can invoke what, from which agent, with full on-behalf-of attribution.
Supports token-based auth, role-based profiles, and per-agent tool restrictions.
Govern and Harden Tool Behavior at the Gateway
Prevent collisions, override tool definitions, and insert approval flows for sensitive actions.
Standardize tool exposure with guardrails that reflect your security and compliance policies.
Gain Visibility Across Teams and Agents
Monitor tool usage and agent behavior with real-time metrics and audit logs.
Track every invocation, including prompt payloads, tool responses, and usage attribution.

Eliminate Shadow MCP Usage and Enforce Enterprise Governance
Gain full control over MCP adoption, prevent security risks, and ensure compliant AI operations.
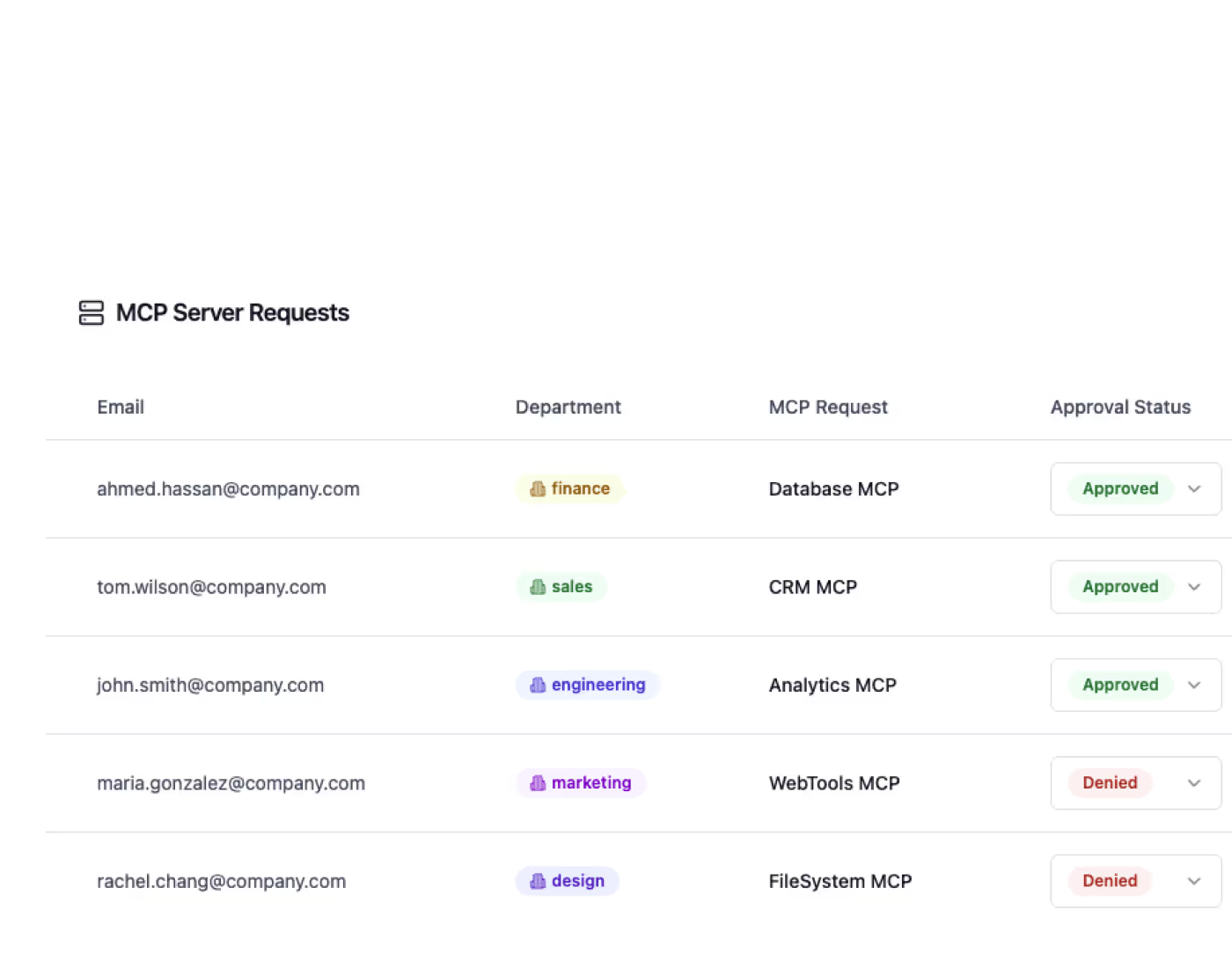
Role-Based Access Control
Define who can use which tools and enforce enterprise policies with granular permissions.
Authentication to MCP Servers
Ensure only approved AI agents and users can access MCP servers with API keys or OAuth.
Real-Time MCP Visibility
Track all MCP usage in real time to detect risks fast. MCPX logs every agent action in an immutable audit trail so you can trace who did what and prove compliance.
Advanced Telemetry
Gain deep insights into tool usage, performance, and security events for governance and optimization.
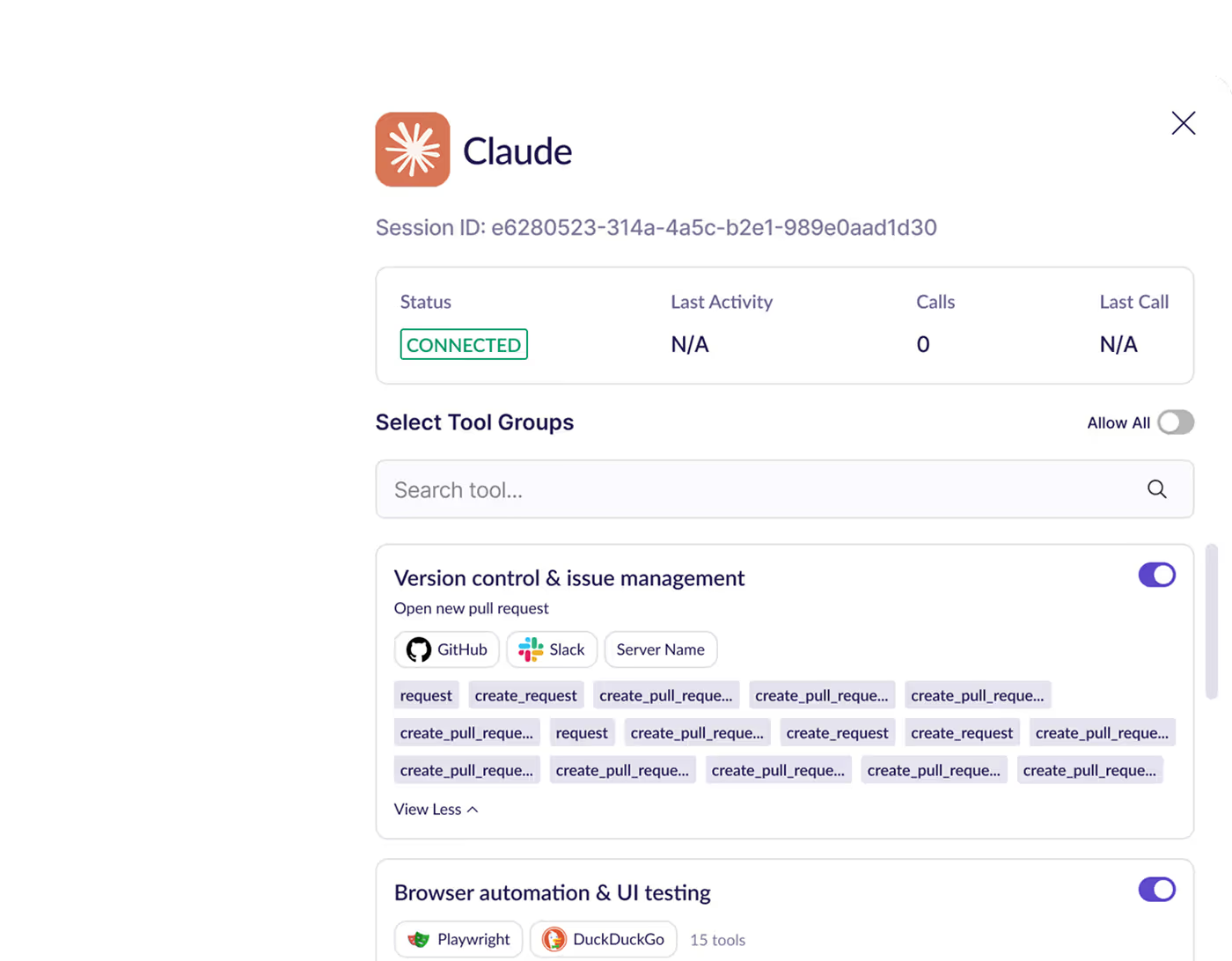
Tool Customization
Adapt or restrict tool behavior to meet compliance, enforce policies, and align with enterprise needs.
SSO and IAM Integrations
Simplify secure access with SSO and connect to your company’s IAM system for centralized user management and governance.
Enterprise MCP Workflow Blueprint
.avif)
Centralize Your MCP Server Registry
Register all internal and external MCP servers centrally.
Discover authorized servers through one unified portal.
Manage local and remote MCP servers in one place.
Prevent shadow usage with a vetted server inventory.
Build Role‑Based Profiles
Authenticate users via Okta, Azure AD, or similar.
Assign roles with tailored access to tools and servers.
Apply rate limits and budget constraints by role.
Enforce company guardrails with identity‑linked profiles.
Observe Everything in Real Time
Capture telemetry for every MCP and tool call.
Stream logs to your existing monitoring or SIEM.
View real‑time dashboards and alerts for anomalies.
Maintain a complete audit trail for compliance.
Operate Safely and Compliantly
Approve or deny requests to access new MCP servers.
Fine‑tune tool descriptions for accuracy and cost.
Apply policy workflows to all operational changes.
Ensure every action meets security and compliance.

Empower Users Without Blocking Them
Provide each user a dedicated, policy‑enforced workspace.
Allow customization within prescribed guardrails.
Encourage innovation while maintaining governance.
Simplify workflows without sacrificing control.
Connect to Lunar’s AI Gateway
Integrate MCP and LLM visibility in one dashboard.
Track costs and prioritize user requests intelligently.
Sanitize data and enforce usage limits seamlessly.
Understand how MCP calls invoke underlying APIs.

Enterprise‑Grade Assurance
Your data, your rules—secure operations across any environment.

Trusted Compliance & DLP Safeguards
SOC 2 certified to protect sensitive information. Built‑in DLP via the Lunar Gateway detects and stops data leaks.
Unified Oversight & Role Management
Single Sign‑On, granular roles, and comprehensive audit logs give you end‑to‑end control over every user and agent action.
Dedicated Support & Fault‑Tolerant Design
Around‑the‑clock enterprise support and SLA‑driven response times, backed by an architecture optimized for resilience.
Private Deployment & Data Sovereignty
Run MCPX within your own cloud or on‑premises environment; nothing leaves your domain, so data remains under your full control.
Frequently asked questions
Yes. MCPX runs as a Docker container and launches other MCP servers within it in real time. Enforcement logic (auth, policies) moves from the agent into the gateway, so agents become simpler and the gateway controls everything. See the Quick Start guide for deployment details.
The open‑source edition is aimed at personal use; it runs locally via Docker. The enterprise edition is designed for production: you deploy it in your own cloud or data center, with centralized management, role‑based access control, auditing and advanced observability.
MCPX mitigates excessive agency risk by preventing agents from getting over‑privileged. Policies such as Access Control Lists (ACLs) and role‑based profiles restrict which tools and methods an agent can call. Basic API key and OAuth support add authentication, and the enterprise edition provides data‑loss prevention to redact sensitive content.
The enterprise edition can inspect requests and responses to redact sensitive data, but everything runs within your environment. Lunar.dev sees only anonymized metrics; your raw data stays inside your VPC or on‑prem deployment.
Yes. You can use ACLs and consumer tags to restrict tools per agent, and Tool Customization lets you create safe variants of tools with fixed parameters. These controls simplify the tool list and prevent agents from calling unnecessary or risky functions.
MCPX exposes Prometheus metrics for each tool call, including labels for the tool name, agent, error status and optional LLM provider and model. When connected to the Lunar AI Gateway, you also see token and cost usage by agent or application in the control plane.
Yes. You can run MCPX alongside the Lunar AI Gateway by setting LUNAR_API_KEY (for the hosted gateway) or LUNAR_URL (for a self‑hosted gateway) and granting NET_ADMIN capability. For instructions, see the Lunar Gateway Integration page.
The MCP evaluation sandbox is an enterprise‑only feature that unboxes MCP servers into a safe testing environment. It routes agent traffic through a separate instance so you can observe behavior, performance and potential data leaks before deploying a server in production. Lunar.dev is currently the only provider offering this deep visibility into MCP server safety.
Additional Resources
See MCPX in Action
Discover the benefits of centralized MCP management. Request beta access to Lunar.dev's MCP Gateway today.










