
Emerging Patterns and Practices for MCP Servers
This post explores emerging best practices for governing MCP and AI agents in production. It covers how leading teams manage tool complexity, enforce determinism, improve security, and centralize control through enterprise grade architecture.
As MCP (Model Context Protocol) adoption moves from experimentation to production, a clear pattern is emerging: the hard problems are no longer about connecting tools — they’re about controlling complexity.
Early MCP demos often look deceptively simple: expose APIs as tools, point an agent at them, and let the model reason. But as Microsoft, Anthropic, and Gartner have independently observed, scale changes everything. Large tool catalogs, overlapping capabilities, local execution, and weak governance quickly degrade reliability, security, and cost efficiency.
This post outlines the emerging practices teams are converging on — and how Lunar’s MCPX platform operationalizes them in production environments.
.png)
1. Context Window Efficiency Is Now a First-Class Constraint
Modern LLMs reason within finite context windows. Every tool definition, schema, and response competes with user intent, conversation history, and system prompts for space.
Microsoft’s research on tool-space interference shows that as tool descriptions grow — or become redundant — models spend more tokens reasoning about tools instead of solving the task. Anthropic similarly emphasizes that excessive or noisy tool metadata degrades both selection accuracy and downstream reasoning.
The emerging practice is to treat context as a scarce resource:
- Minimize tool descriptions
- Return compact, task-oriented responses
- Avoid passing raw API payloads directly to the model
How Lunar fits
Lunar MCPX enforces context efficiency at multiple layers:
- Tool Groups allow only the relevant subset of tools to be exposed per agent, task, or role
- Tool customization allowing to override tool description to shorten and customize tool descriptions, to better fit company’s needs within a budget constraint
- Keeping track on token count for each tools, and understanding the overall sum of token usage for a group of tools in a context window
- Gateway-level response shaping ensures tools return LLM-friendly outputs, not verbose API objects
This shifts context optimization from an application concern into platform-level hygiene.
2. Deterministic Tool Orchestration Beats Probabilistic Chaining
LLMs are excellent at intent detection — but less reliable at executing strict, multi-step workflows. Microsoft highlights that probabilistic chaining becomes fragile when workflows require ordering, retries, or transactional guarantees. Anthropic reaches the same conclusion for advanced tool use: some logic must move out of the model.
The emerging pattern is to:
- Start with granular tools during discovery
- Observe repeated call sequences
- Replace them with composite tools that encapsulate orchestration deterministically
This reduces latency, token usage, and failure modes.
How Lunar fits
Lunar is introducing composite tools (contact us for beta access!) that:
- Expose a single outcome-oriented tool to the model
- Execute ordered workflows behind the scenes
- Preserve determinism while keeping intent recognition with the LLM
.png)
This allows teams to move orchestration logic out of prompts and into governed infrastructure — where it can be tested, versioned, and audited.
3. Tool Count Must Be Actively Managed — Not Left to Chance
A recurring failure mode across MCP deployments is uncontrolled tool growth. As Gartner notes, tool overload degrades selection accuracy even before context limits are reached. Microsoft’s work further shows that overlapping or semantically similar tools confuse the model’s internal ranking.
The emerging practice is not just “fewer tools”, but intentional exposure:
- Limit active tools per session
- Group tools by domain or task
- Avoid overlapping responsibilities
How Lunar fits
Lunar’s Tool Groups are purpose-built for this problem:
- Tools are curated into logical, non-overlapping sets
- Agents only see the tools they actually need
- Groups can be dynamically assigned by identity, environment, or workload
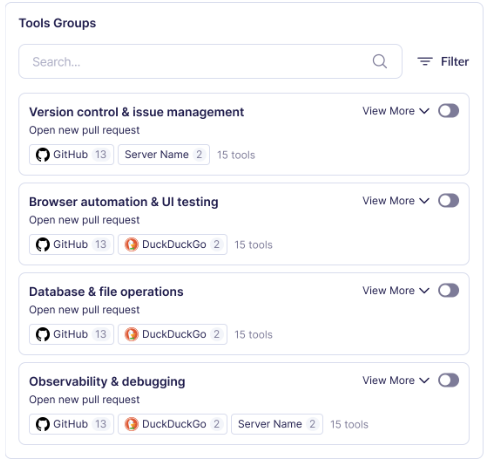
This transforms tool selection from a static registry problem into a runtime control surface.
4. Tool Customization Is Becoming Essential for Safe Reuse
An emerging gap not fully addressed in public research is what happens when teams consume third-party or open-source MCP tools. These tools often:
- Return overly verbose responses
- Expose unsafe parameters
- Lack enterprise-grade constraints
The naive approach is to fork or rewrite them — which breaks update paths and ownership models.
The emerging practice is tool adaptation, not replacement.
How Lunar fits
Lunar MCPX introduces Tool Customization, allowing teams to:
- Wrap untrusted tools with stricter schemas
- Redact or reshape responses before they reach the model
Add guardrails without modifying upstream code
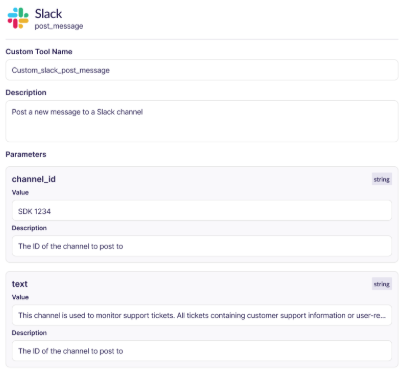
This enables safe reuse of community MCP servers while enforcing enterprise standards — a critical capability as MCP ecosystems expand.
5. Remote-First MCP, With Guarded Local Exceptions
Local MCP servers are convenient — and dangerous. They run with user privileges, bypass centralized logging, and are hard to inventory. Both Gartner and Microsoft observe that unmanaged local servers become blind spots for security and compliance.
The emerging model is:
- Default to remote MCP servers
- Treat local servers as exceptions
- Enforce isolation, allow-listing, and observability when local use is unavoidable
How Lunar fits
Lunar MCPX supports:
- Remote-first MCP consumption through a centralized gateway
- Containerized execution for local or third-party servers
- Registry-based allow-listing to control what can run
This preserves developer flexibility without sacrificing security posture.
6. Gateway-Centric Governance Is No Longer Optional
As MCP usage spreads across teams, tools, and agents, governance cannot live inside individual servers. Authentication, authorization, rate limits, and audit logs must be centralized - exactly as API gateways evolved in microservices architectures.
The emerging practice is a dedicated MCP-aware gateway that:
- Mediates all MCP traffic
- Integrates with enterprise identity providers
- Provides full observability and policy enforcement
How Lunar fits
Lunar MCPX acts as a native MCP Gateway, offering:
- Centralized auth and access control
- Policy enforcement per tool, group, or identity
- End-to-end visibility into agent-tool interactions
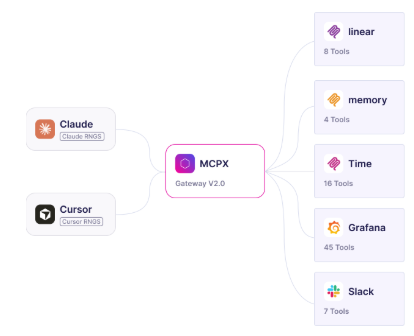
This transforms MCP from a collection of scripts into a governed production platform.
Closing Thoughts
The MCP ecosystem is maturing fast — and with maturity comes architectural discipline. The teams succeeding with MCP are not writing clever prompts; they are designing systems that respect model constraints, reduce ambiguity, and centralize control.
Lunar’s approach reflects this shift: moving responsibility out of agents and into infrastructure. As MCP adoption grows, these patterns won’t be optional — they’ll be the baseline.
Ready to Start your journey?
Manage a single service and unlock API management at scale


.png)
.png)


